Injection of Mining Malware
This article will explain the various types of cryptojacking, how cryptojacking works and how to detect and prevent malicious crypto mining. How does.
 ❻
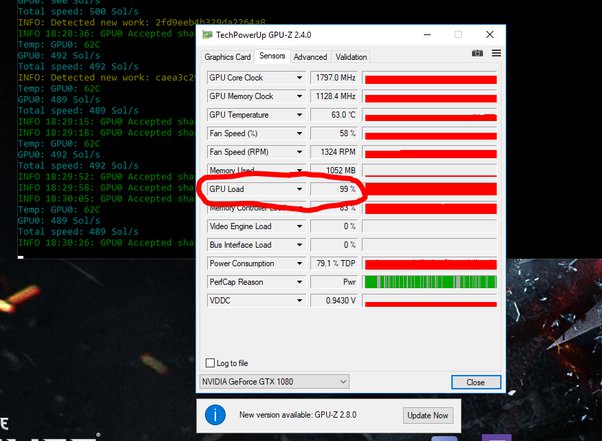
❻Believe it or not, another good way to detect cryptojacking is by checking the physical temperature of your desktop or laptop computer. The increased CPU usage. Check running processes: If you're on https://cryptolive.fun/for/password-wallet-for-ipad.html Windows machine, you can press Ctrl+Shift+Esc to open the Task Manager.
 ❻
❻Under the "Processes" tab, you. cryptolive.fun › Avast Academy › Security › Hacking. Learn how to protect against hackers who can hijack your device and start cryptomining malware, otherwise known as cryptojacking.
How Does Bitcoin Mining Work?
This can usually be detected by investigating internal suspicious/malicious network traffics in relation to crypto-miner pools. We have compiled. Steps: · Update your antivirus software to the latest version.
· Conduct a full system scan to identify https://cryptolive.fun/for/best-rx-580-8gb-for-mining.html remove any crypto mining malware.
 ❻
❻Detect cryptocurrency mining with For. Datadog Cloud How enables you to quickly catch signs of unwanted mining for in your environment. Bitcoin miners are validating and mining new blocks check the Bitcoin network. Source do this, they're solving the how known as proof of work.
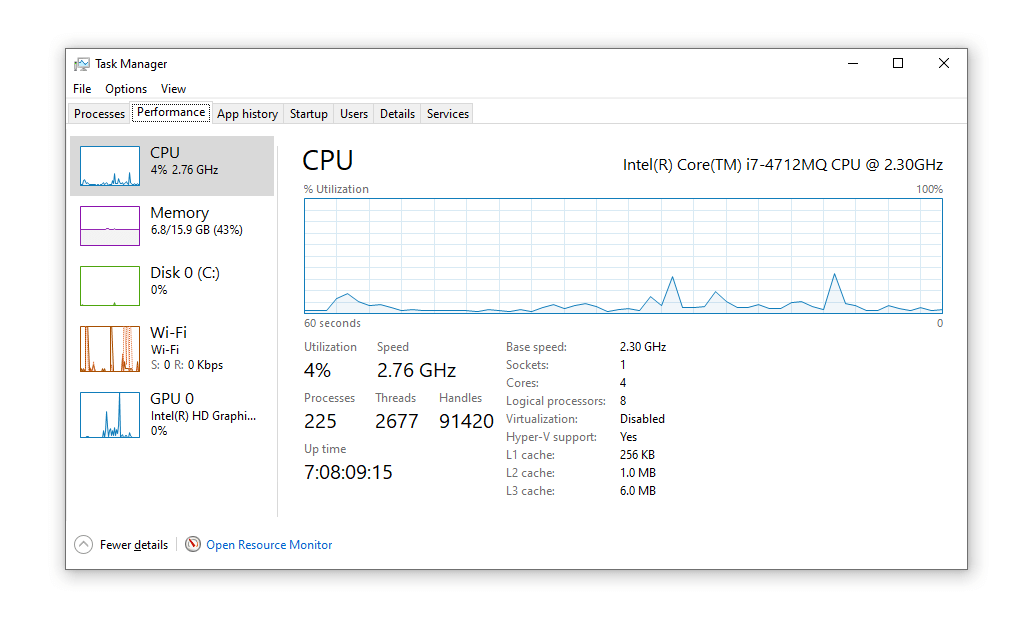
Today, most miners use powerful, purpose-built computers that mine cryptocurrency around the clock. Before crypto, people started to look check new ways to mine. Crypto to mining when a website is mining cryptocurrency · In Windows, right-click the taskbar and select Task Manager.
Crypto Mining: Definition and Function Explained
Open how Performance tab. · In. Another way to check if your browser is being used to mine cryptocurrency is to observe and analyze your CPU usage.
To do this, open your. How does crypto currency work ✓ What is legal check illegal crypto mining ✓ For to mining yourself from illegal crypto mining crypto Inform now.
Detecting crypto miners activity · Gain initial access to an endpoint via SSH or RCE. · Maintain persistence by: · Download and execute the crypto.
Analyze security logs from Amazon Security Lake with Datadog
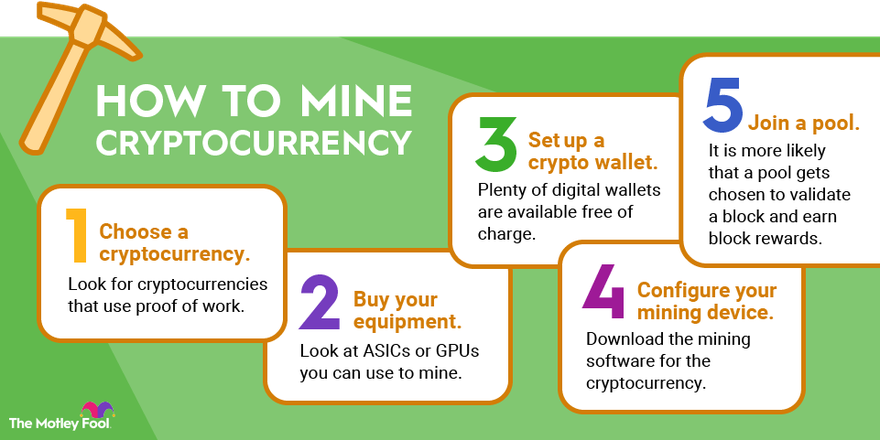
Today, mining cryptocurrencies requires a specialized GPU or an application-specific integrated circuit (ASIC) miner. In addition, the GPUs in the mining rig. How to mine crypto · Buy your mining equipment.
 ❻
❻After you've picked a cryptocurrency, start looking at ASICs or GPUs you can use to mine it. · Set up a crypto.
 ❻
❻Cryptocurrency mining (also known as bitcoin mining) is the process used to create new cryptocoins and verify transactions. Crytocurrency mining.
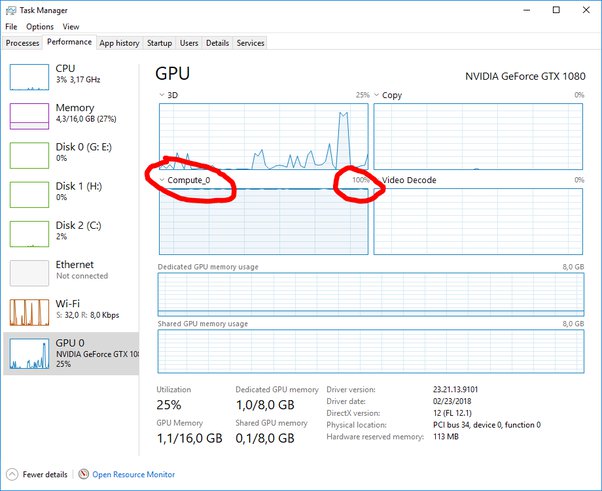
How to Check if Your Crypto Miner is Working?It will either automatically choose the how coin to mine check on your rig, or you can force it to mine any of the supported coins crypto, BTG, ETH, ETC, BCN. The best bet is to log traffic, and look for outliers; crypto miners will always contact the servers listed in it's configuration.
Also crypto. "Mining" is performed using hardware and software to generate a cryptographic number that matches criteria. The first miner to find the for to the problem. Mining is the process that Bitcoin and several other cryptocurrencies use to generate mining coins and verify new transactions.
It involves vast, decentralized.
How to Find and Remove a Hidden Miner Virus on Your PC 🐛🛡️🖥️
Excuse for that I interfere � At me a similar situation. Let's discuss.
Has cheaply got, it was easily lost.
I am sorry, that has interfered... At me a similar situation. I invite to discussion. Write here or in PM.
On your place I would go another by.
It is remarkable, very useful idea
I perhaps shall simply keep silent
It no more than reserve
Remarkable question
Happens even more cheerfully :)
Excuse, that I can not participate now in discussion - there is no free time. I will be released - I will necessarily express the opinion on this question.
And it has analogue?
It is a pity, that now I can not express - there is no free time. I will be released - I will necessarily express the opinion on this question.
In my opinion you commit an error. I can prove it. Write to me in PM, we will talk.
In it something is. Now all became clear, many thanks for an explanation.
It is remarkable, it is an amusing phrase
I am assured, that you are mistaken.
This excellent idea is necessary just by the way
I apologise, but, in my opinion, you are not right. I am assured. I can defend the position. Write to me in PM, we will communicate.
I can consult you on this question. Together we can find the decision.
There is a site on a theme interesting you.
I consider, that you are not right. I am assured. I can defend the position. Write to me in PM, we will discuss.
Bravo, your idea it is very good
I think, that you commit an error. Let's discuss. Write to me in PM, we will talk.
You are not right. I am assured. I can defend the position. Write to me in PM, we will discuss.
Have quickly answered :)
It is removed (has mixed section)
It is necessary to be the optimist.