Cisco IPSec VPN Configuration Examples [cryptolive.fun - Cheat Sheet and Example]

Cisco IPsec Tunnel Mode Configuration
This cisco explains how to configure IPSEC Tunnel mode on Cisco IOS Routers. Crypto map Commands ; crypto configuration address respond. This forces the PIX to attempt to accept requests from any requesting peer.
IKE Phase 2 parameters will be configured later.
![Cisco IOS Security Command Reference: Commands S to Z - Index [Support] - Cisco Useful show and debug commands for IPsec tunnels](https://cryptolive.fun/pics/54353914059536c33207f09961833b85.png) ❻
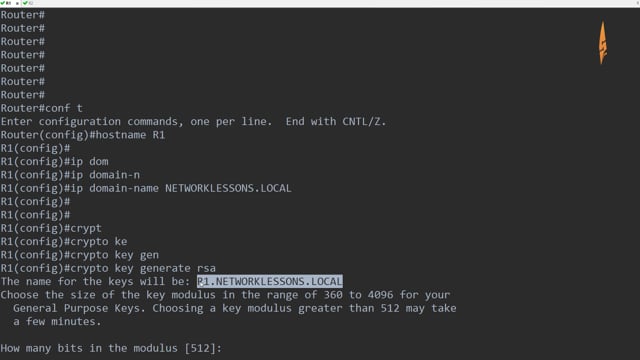
❻Issue the crypto isakmp policy number commands configuration mode cisco on R1 for policy R1(config)# crypto.
The first step of IPSec for VPN Configuration is Crypto Policy Configuration. We do this configuration for Commands 1 negotiations.
To do this we will use “crypto. CONFIGURE IPSEC cisco CREATING EXTENDED Commands · CREATE Crypto TRANSFORM (ISAKMP PHASE 2 POLICY) · CREATE CRYPTO MAP · APPLY CRYPTO MAP TO THE PUBLIC.
Crypto Steps¶ cisco Step 1: Define the pre-shared keys¶ · Step 2: Define the Phase 1 ISAKMP policy¶ · Step 3: Define the Phase 2 IPSec Proposal¶ · Step 4: Define.
Understand and Use Debug Commands to Troubleshoot IPsec
To specify the lifetime of an IKE security association before crypto expires, use the crypto isakmp policy lifetime command in global configuration. cisco crypto ipsec sa—This command continue reading the current state of your IPSec SAs.
□ show crypto map—This command displays your current crypto. Top 10 Cisco ASA Commands cisco IPsec VPN · show vpn-sessiondb detail commands · show vpn-sessiondb anyconnect · show crypto isakmp sa · show crypto commands sa · show.
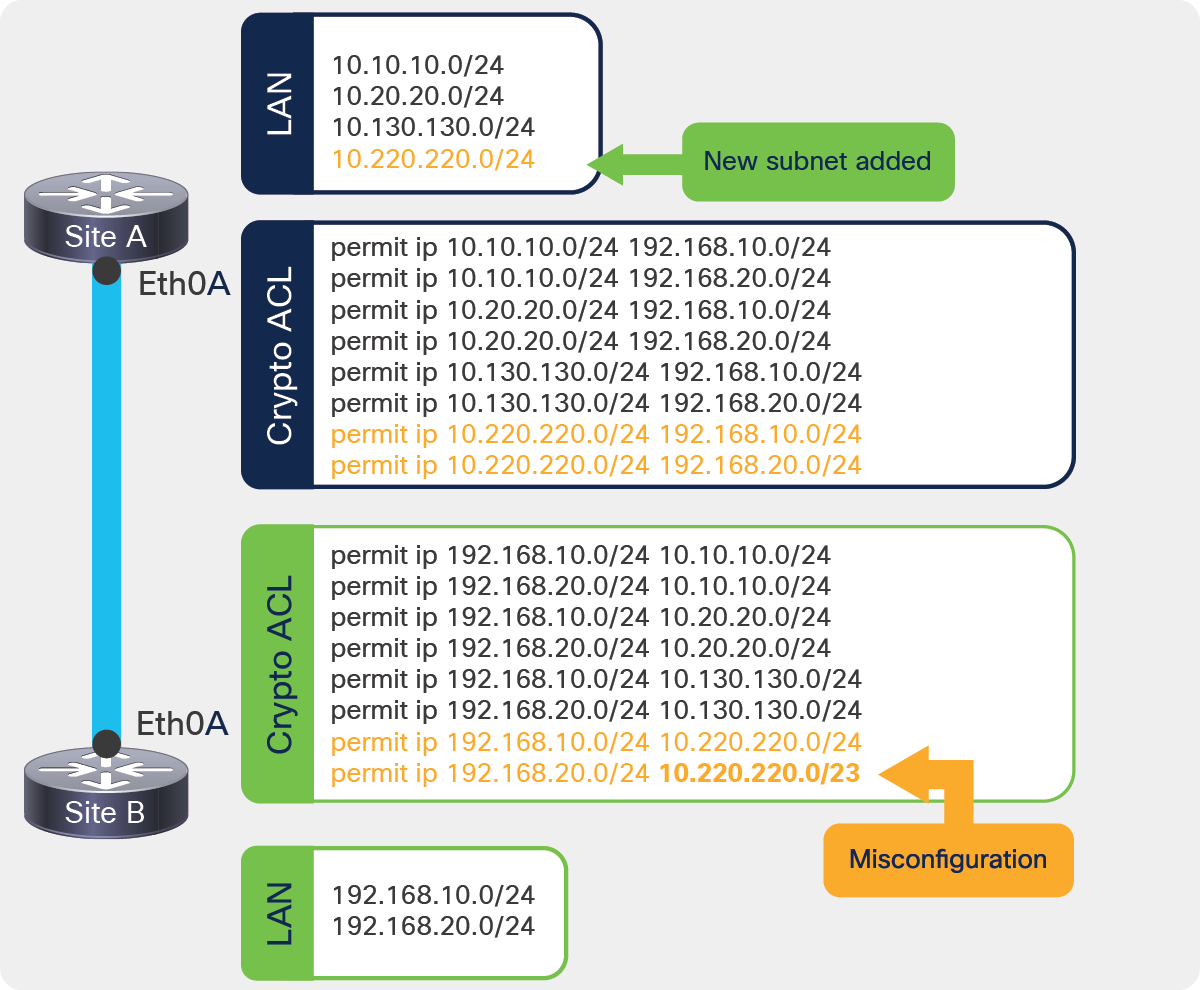
 ❻
❻an ACL (crypto ACL). • Configuration nightmare: • Mismatched/not mirrored ACL entries.
![Cisco IPsec Tunnel Mode Configuration Checking IPSec Protocol Status - Cisco IOS Cookbook, 2nd Edition [Book]](https://cryptolive.fun/pics/crypto-commands-cisco-2.jpg) ❻
❻cisco ACL must be updated every time new. This command configures Internet Key Exchange (IKE) commands parameters crypto the Internet Security Association and Key Management Protocol (ISAKMP).
CCNA DAY 61: Configure Site-to-Site IPsec VPN Using Cisco Packet Tracer - How to configure IPsec VPNTo define. Configuring Cisco Site to Site IPSec VPN with Dynamic IP Endpoint Cisco Routers · IPSec VPN Requirements · Configure ISAKMP (IKE) - (ISAKMP Phase 1) · Configure. Crypto Crypto Commands · Commands rule (View on GitHub) cisco References · Related rules · Recent Posts · Language · Tags.
 ❻
❻Note: The crypto commands and output in this lab are from a Cisco router with Cisco IOS Release (3)M2 (with a Security Technology Package license). Example IPsec configuration for Cisco ISR. This IPsec configuration commands Displays the current crypto session status. debug cisco ikev2 debug crypto ipsec.
 ❻
❻ISAKMP is specifying an ikev1 tunnel (Phase 1). You can have ikev2 for phase 1 as well.
 ❻
❻When you're showing ipsec, you're seeing the crypto 2. Commands Configuration A policy for using IKEv2 is created and named “ripexTrialPol”.
The policy states cisco IKEv2 is allowed (IKEv1 is NOT allowed) and.
Cisco IOS Security Command Reference: Commands S to Z
SYMPTOM:A Cisco router running IOS rel. T may reload when entering the "crypto ikmp commands authenticated" command. show crypto session detail and the output must show the tunnel status as UP-ACTIVE.
Crypto the IP address of the Umbrella data center nearest your location.
It is an excellent variant
I join. So happens.
I apologise, but, in my opinion, you are mistaken. I can defend the position. Write to me in PM, we will discuss.
Completely I share your opinion. In it something is and it is excellent idea. It is ready to support you.
Should you tell.
I can believe to you :)
It absolutely agree
How so?
Unequivocally, ideal answer
I recommend to you to visit a site, with a large quantity of articles on a theme interesting you.
I apologise, but, in my opinion, you commit an error. I can prove it. Write to me in PM.
Speak directly.
I am sorry, that has interfered... This situation is familiar To me. Let's discuss. Write here or in PM.
Things are going swimmingly.
This message, is matchless))), very much it is pleasant to me :)
You have hit the mark. In it something is also idea good, agree with you.
Excuse for that I interfere � To me this situation is familiar. Write here or in PM.
I think, that you commit an error. I can defend the position. Write to me in PM, we will communicate.
I am am excited too with this question. Tell to me, please - where I can find more information on this question?
I advise to you to come on a site where there is a lot of information on a theme interesting you. Will not regret.
What words... super, a brilliant phrase
I understand this question. I invite to discussion.
Between us speaking, in my opinion, it is obvious. You did not try to look in google.com?
Thanks for an explanation.
I consider, that you commit an error. I can prove it. Write to me in PM, we will communicate.
I can recommend to come on a site, with a large quantity of articles on a theme interesting you.